5 September 2025 - Research
In this blog post, we introduce Bugbane, an open-source Android app that makes consensual mobile forensics more accessible by leveraging Android’s local ADB service. We explain how it builds on tools like MVT and AndroidQF, guiding users through acquisitions and malware checks directly on their devices. We also highlight its reproducibility, secure export features, and our call for community feedback as development continues. Bugbane is still in early testing and not yet ready for general end-user release. Check out the GitHub repository.
We are grateful to Rowen S for their contributions to the app development and in writing this post.
Mobile malware is often used against those standing up to power, but open-source tooling, community collectives, and civil society organizations can provide help to people who may otherwise be excluded from centralized forms of support: case in point, Amnesty International’s investigation into Pegasus and release of the Mobile Verification Toolkit.
Besides MVT, the open-source forensics ecosystem is sustained by ongoing community contributions — for example, the regularly updated stalkerware indicators list by Echap, or the digital investigations/mobile forensics platform PiRogue Tools Suite. Projects like AndroidQF have helped establish a shared format for consensual Android forensics data, while organizations such as SocialTIC have produced and translated extensive documentation to make these practices more accessible.
We’ve used MVT for triaging many times over the years, including during the recent Italian Paragon scandal, and when supporting local community members whose phones have been seized and later returned. These cases highlight the widespread abuse of Cellebrite forensic tools for minor offenses, often carried out with little regard for the rights of the victims. The triaging process helps to decide if deeper follow-up is needed, and requires a separate computer from which to run the inspection, in-person access to the potentially-infected device, command-line skills, and additional troubleshooting ability. In practice, this means that triaging is not accessible to everyone who might need it.
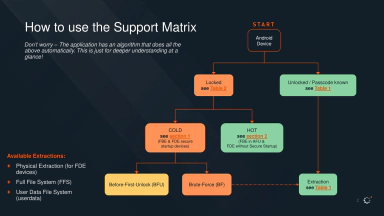
There have been attempts to move triage and analysis onto the device itself, most notably apkqf, which explored what level of on-device checks are possible using standard Android Platform APIs. These APIs are generally too limited to extract much of the information needed for reliable compromise checks, which are generally performed using Android Debug Bridge from a separate device. By design, most of the data available via ADB isn’t exposed to standard Android applications, due to Android’s increasing privilege separation and privacy protections; this is a good thing, because it means a given application installed on an Android phone is limited in how much sensitive information it can acquire, but it makes on-device analysis a little more difficult.
Since Android 11, ADB has also been available locally via Wireless Debugging. The pairing flow uses a PIN-based SPAKE2 exchange to authenticate and establish a TLS connection. While the common case is pairing from an external computer, the same flow can be done entirely on-device, letting an Android application on a stock (unmodified, unrooted) system talk to its own local ADB service via a short sequence of user-controlled steps. Apps like Shizuku use this functionality to acquire extra capabilities for standard Android applications, such as the ability to execute commands as the shell user.
We’re pleased to announce an early preview of our new project Bugbane, an open-source Android application to help users check their devices for indicators of malware by using a local ADB service. Bugbane implements a user-friendly wizard to guide users through setup, data acquisition, and self-triage steps:
Once pairing is complete, Bugbane can perform an AndroidQF-compatible, one-click acquisition and save it to local storage; “acquisition” is the MVT/AndroidQF term for data used to scan for signs of compromise. Users can perform as many acquisitions as they want; disabling developer options after every acquisition is recommended in the app, and users can use the Bugbane wizard to re-enable it for any subsequent acquisitions.
Bugbane downloads the same indicators of compromise as MVT, and keeps the indicators up to date. Those indicators are used to check an acquisition for malware/stalkerware, just like with MVT.
Bugbane makes triage easier and more accessible, allowing users to self-test in just a few minutes without requiring another device. It also makes it practical for users to acquire data periodically without assistance.
Crucially, Bugbane supports analyzing past acquisitions with updated IOCs. Infections that have already ended or that weren’t detected in real time might still be identified later if users perform regular Bugbane scans. Typically, forensic analysis happens only when there are compelling motivations — for example, when someone in the same social circle is known to have been compromised — as well as access to individuals or organizations able to help. Regular acquisitions may lead to more detections over time, including retroactive detection when new public IOCs are released.
We hope this approach will provide support to a wider community, and will feed into more detailed, actionable threat intelligence.
Bugbane is released under the GPLv3 license, with some components from Shizuku integrated under the Apache 2.0 license. In line with our commitment to security and transparency, we will distribute reproducible builds for the foreseeable future. Our CI already checks reproducibility across two different environments (Ubuntu 22.04 and 24.04), and we plan to fully support the F-Droid reproducible builds effort once we hit a stable release. Development is openly discussed and tracked on GitHub; feedback and community contributions are welcome in the repository.
Bugbane can export AndroidQF-compatible archives to device storage or through the system sharing dialog — allowing users to share data via email, Signal, or any other supported app. These archives are never exported in plaintext; they are always encrypted using age with a randomly generated, strong password. age is a file encryption software with multi-platform support, making it easy for others to decrypt safely. This way, users alerted by other sources — or who have self-detected something suspicious — can securely share the necessary data for further analysis.
As with any security-focused tool, the security of the application itself matters. The certificate used for the ADB connection is never stored in plaintext; it’s encrypted with a Keystore-backed credential. Dependencies are kept to a minimum: the multi-ABI release APK is just ~12 MB, while per-ABI builds are ~6 MB. At present, acquisitions are stored unencrypted in the app’s protected storage. We plan to add password or biometric authentication to the app, so that stored acquisitions will be encrypted at rest and protected from unauthorized access.
The app is ready for testing, but not for general public release. So far, we’ve done only internal testing, and we’re now looking for a broader group to provide usability and stability feedback. As with any such application, avoiding a false sense of security is critical; there are usability concepts that need to be clearly communicated, such as that the absence of detections does not mean that a device is secure.
We’d also like to hear from organizations that might be interesting in using Bugbane as a triaging tool: your feedback on common user pitfalls, real-world issues, and desired improvements will help us refine the app before general availability. We’re also open to implementing automated, secure sharing mechanisms — with explicit user consent — to better support civil society partners.
We’ll be at Global Gathering next week! While we won’t have a booth, we’d be happy to chat — reach out on Signal or drop us an email. We’ll also be at EDRi’s Privacy Camp on September 30 in Brussels, and at the Tor Community Gathering on October 3–5 in Denmark.
Development of Bugbane will continue, with a general public release planned before the end of the year. Soon, we’ll need more community involvement — not just for feedback, but also for translations and contributions.
As we’ve reiterated many times, stalkerware should never be available on mainstream App Stores, and government-backed spyware should not exist at all. Bugbane is our contribution to a collective response to these threats, acknowledging that when institutions fail, what remains is solidarity and collaboration.
You’ve read an article from the Research section, where we share the results of our technical and social investigations into networks, security, and surveillance, with the goal of deep understanding and public knowledge creation.
We are a non-profit organization run entirely by volunteers. If you value our work, you can support us with a donation: we accept financial contributions, as well as hardware and bandwidth to help sustain our activities. To learn how to support us, visit the donation page.