8 March 2025 - Advocacy
In recent years, authorities in several countries have intensified their use of digital surveillance tools to access mobile devices, often without proper adherence to legal procedures and without the informed consent of those affected—sometimes in blatant violation of existing laws, as demonstrated by the current Paragon and Graphite case. Osservatorio Nessuno recently assisted members of the No CPR Torino assembly (a collective opposing Italy’s Centri di Permanenza per il Rimpatrio, detention centers for migrants awaiting deportation) in discovering that their phones had been unlocked and forensically analyzed using Cellebrite tools, without being given sufficient prior notice to allow their legal consultants to verify that the procedure was conducted lawfully.
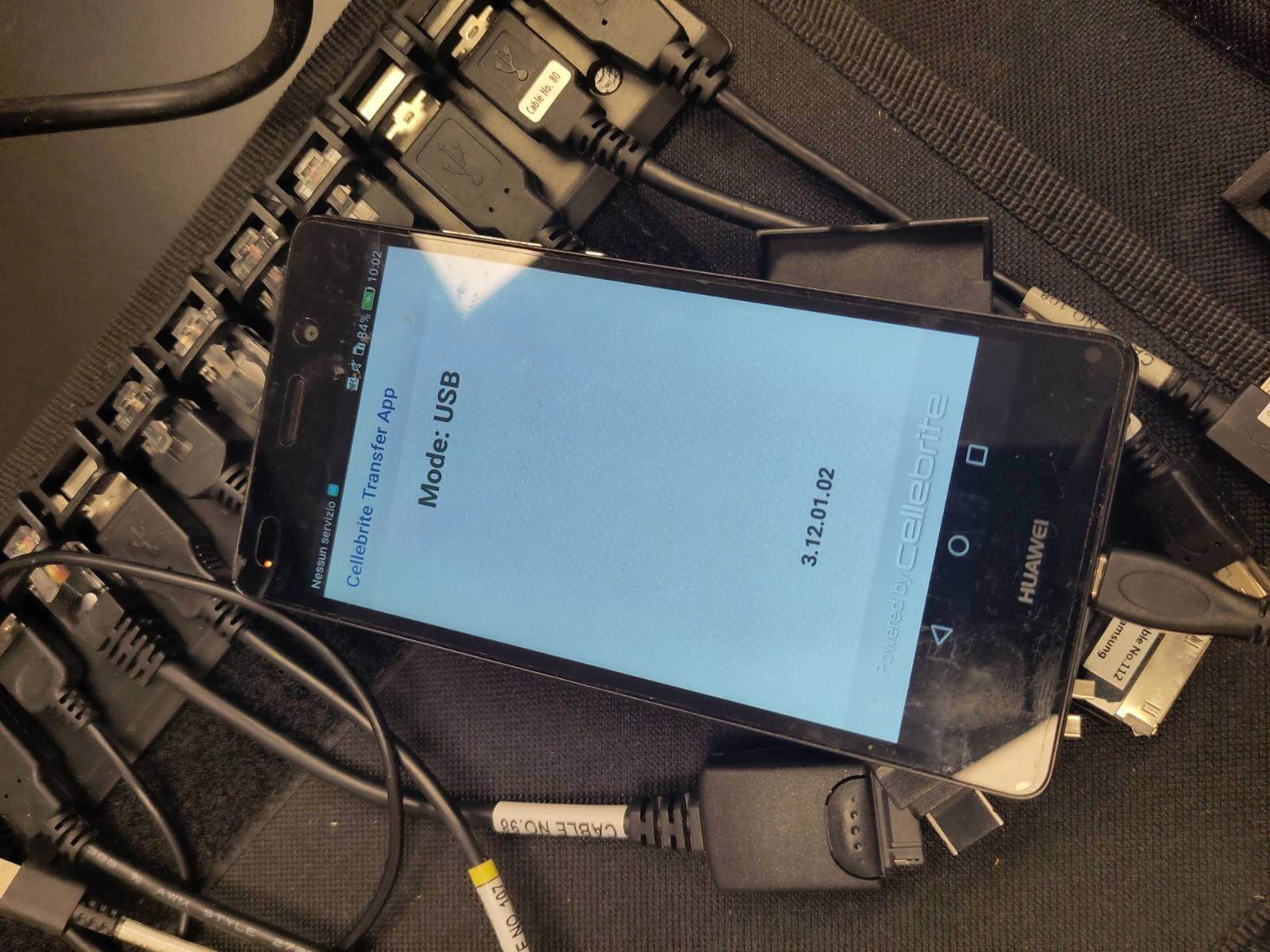
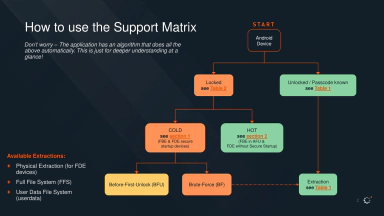
A specific case concerns three phones that were seized on March 20, 2024, during an action at Malpensa Airport. The smartphones, protected by PINs and with encryption enabled, were returned with clear signs of compromise: two of them had their PINs written on a sticker on the back, an evident indication that they had been unlocked and analyzed. As far as we know, the devices were turned off and relatively up to date, requiring an unlock method that, according to Cellebrite’s own terminology, is classified as Before First Unlock (BFU), one of the most technically complex and expensive exploits to develop and acquire.
Using the Mobile Verification Toolkit, we confirmed the compromise and found unequivocal signs of the use of tools from the Israeli company. The extracted files matched those analyzed in a recent Amnesty International report, which denounces the use of Cellebrite and spyware to monitor journalists and activists in Serbia. The connection to Cellebrite and its UFED/Inseyets service suggests that Italian law enforcement sent the devices to third-party consultants who, equipped with these tools, extracted data from the phones without adequately informing the individuals concerned or their legal representatives.
We are currently in contact with international organizations and are assisting in an in-depth technical analysis. The results of this analysis will be published at a later date.
It is not just the pervasiveness of surveillance that is concerning, but also the fact that Cellebrite is active in the 0-day exploit market, which takes advantage of unknown vulnerabilities in operating systems to bypass security measures. This type of trade undermines the security of all users, including governments and businesses, fueling a vicious cycle of cybersecurity threats.
Osservatorio Nessuno strongly condemns the use of tools like Cellebrite against activists, journalists, and ordinary citizens. These tools, marketed as crime-fighting solutions, are instead often used to target political dissent and civil society. Furthermore, the companies that develop and sell them—particularly in the case of Cellebrite—are not required to follow any meaningful vetting process for their customers or users. As a result, they are often freely available for purchase by third parties, including phone shops, consultants, and private companies.
As an organization, we are committed to defending the right to privacy and digital security for everyone, especially those most vulnerable to state surveillance. We will continue to monitor these developments and provide support to anyone who has been a victim of abusive surveillance practices.
If you are an activist or journalist concerned about the security of your devices, or if your device has been seized and you do not have a technical consultant to assist you, contact us via Signal at this link or send an email to support@osservatorionessuno.org.
You’ve read an article from the Advocacy section, where we defend online privacy and anonymity, document threats and invasive practices such as surveillance companies, and promote a conscious and free digital culture.
We are a non-profit organization run entirely by volunteers. If you value our work, you can support us with a donation: we accept financial contributions, as well as hardware and bandwidth to help sustain our activities. To learn how to support us, visit the donation page.